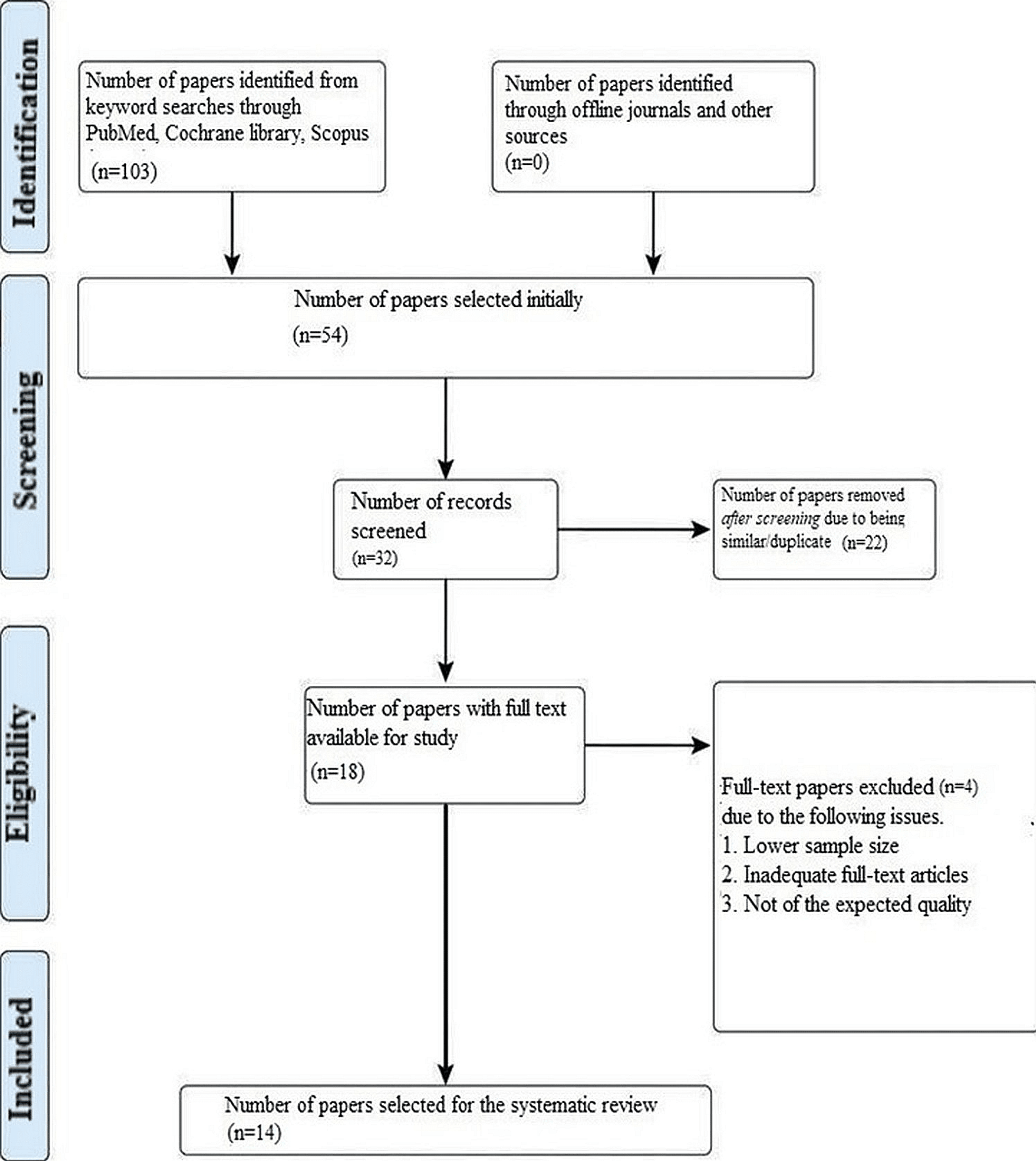
Cambro Cam GoBox® Black Top Loading EPP Insulated Food Pan Carrier - 8" Deep Full-Size Pan Max Capacity
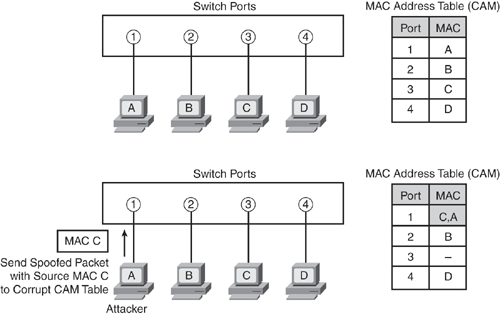
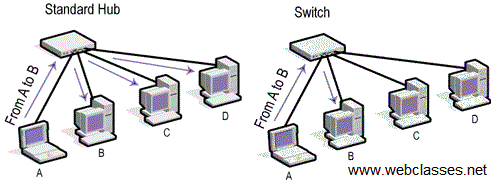
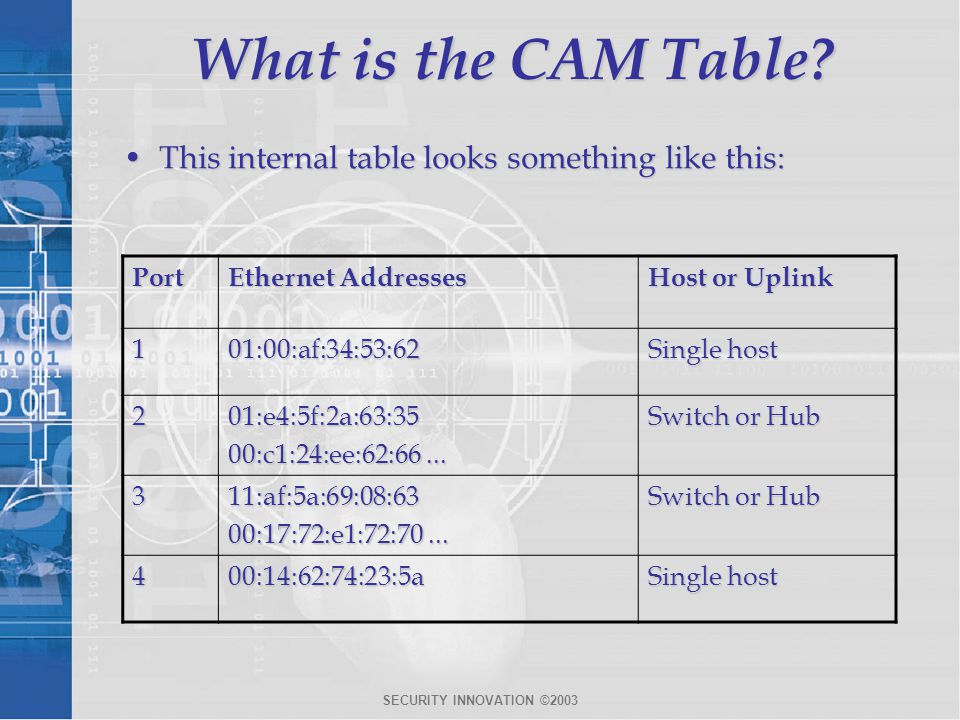
MAC Address Tables | Basic Data Transmission in Networks: MAC Tables and ARP Tables | Pearson IT Certification

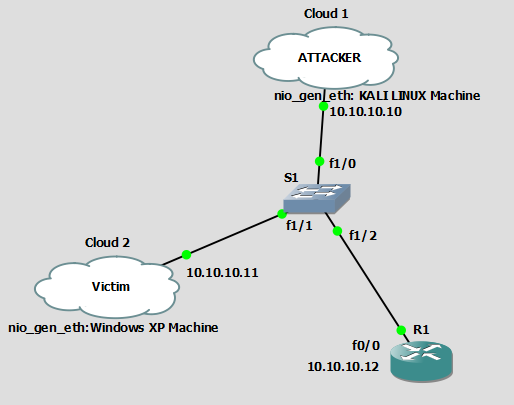
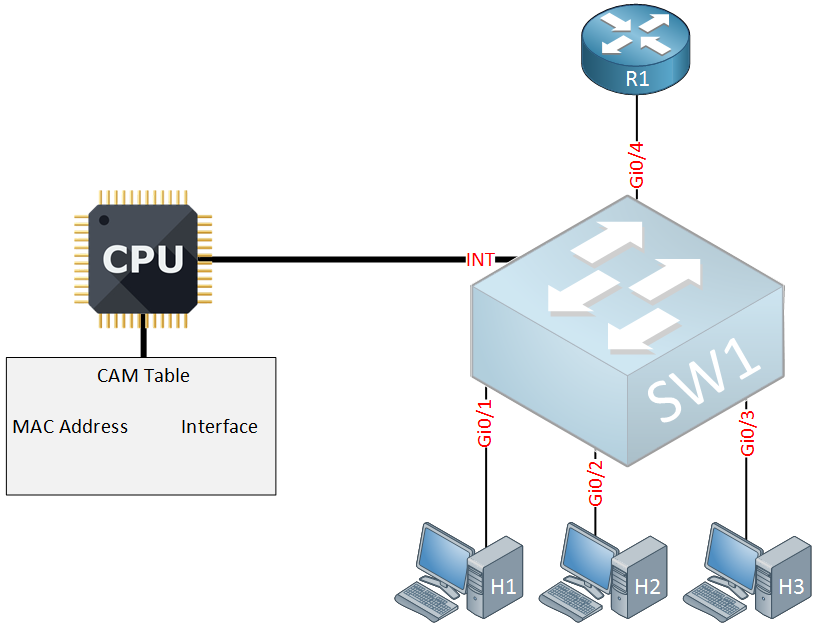
Design and analysis of data link impersonation attack for wired LAN application layer services | SpringerLink


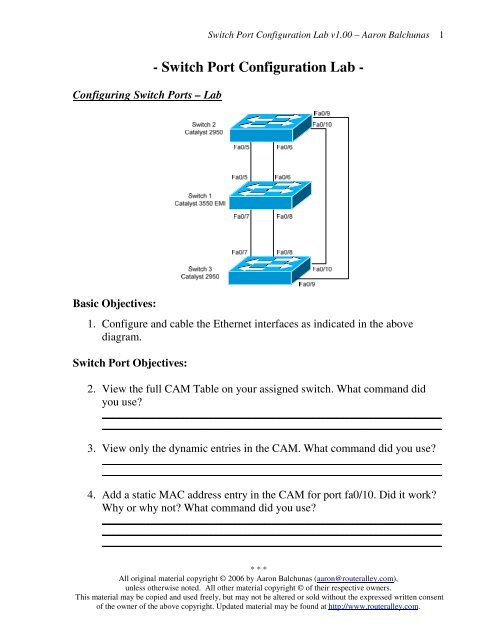
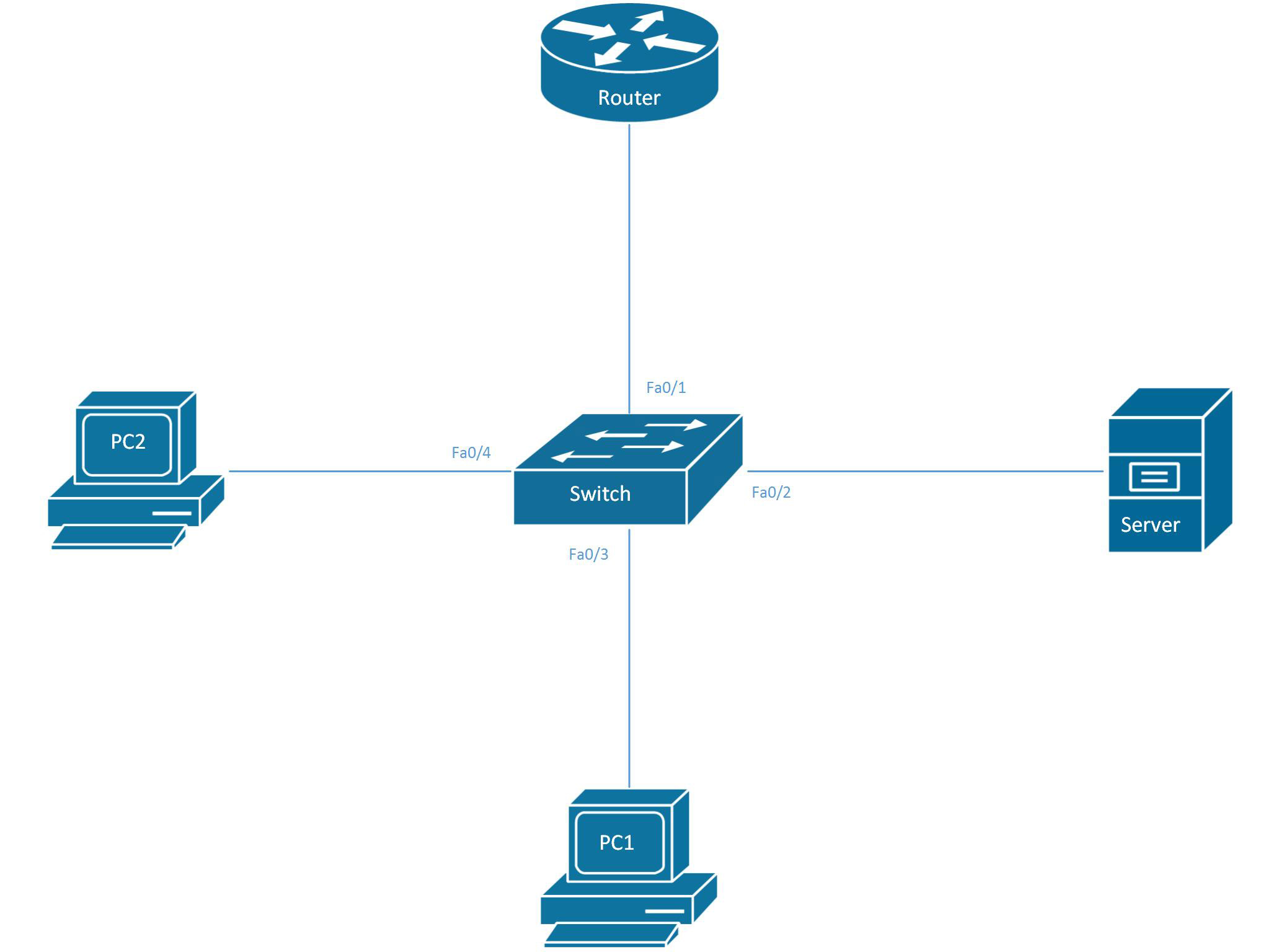
![How the switch uses the CAM tables - Python Penetration Testing Essentials [Book] How the switch uses the CAM tables - Python Penetration Testing Essentials [Book]](https://www.oreilly.com/api/v2/epubs/9781789138962/files/assets/4f76d848-e99f-42e0-b0e0-38b7d139b0df.png)